To set up an F5 load balancer with health monitoring, port-based load balancing, and session persistence, you can follow these steps: Please make sure to consult the official F5 documentation for detailed instructions specific to your F5 load balancer model and firmware version.
Read MoreAuthor: MES ENGINEER
Cloud Technologies & Digital Manufacturing
Using the cloud for digital manufacturing offers numerous benefits for businesses. Here are a few key advantages: To mitigate potential risks when using the cloud for digital manufacturing, consider the following measures: By leveraging the benefits of cloud computing and implementing robust security measures, manufacturers can take full advantage of digital technologies while minimizing potential risks.
Read MoreNetwork Troubleshooting Commands for Windows
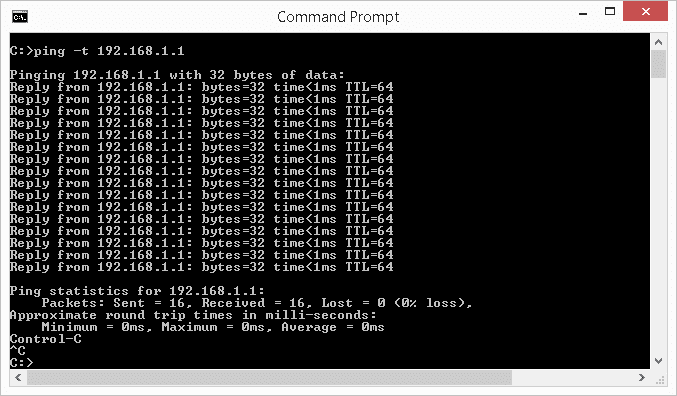
When it comes to troubleshooting network issues on Windows systems, having a strong set of commands at your disposal can help identify and resolve problems efficiently. In this article, we will explore some of the most common network troubleshooting commands for Windows and guide you through their usage. 1. ipconfig The ipconfig command provides valuable information about network interfaces on your Windows machine. It reveals details such as IP addresses, subnet masks, default gateways, and more. Executing ipconfig without any arguments will display essential network configurations for all interfaces. To…
Read MoreDNS Basics (Host A / PTR Record Creation)
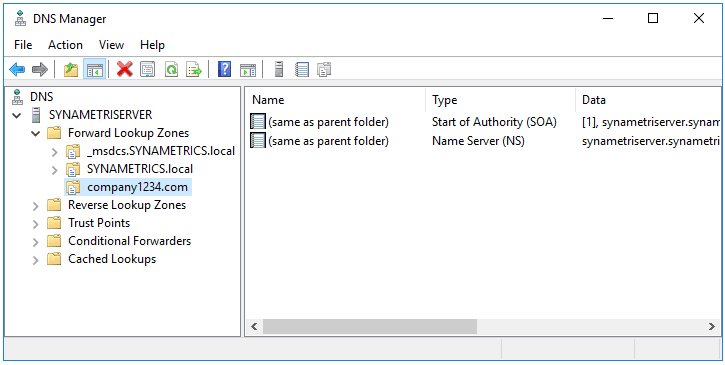
To create a DNS Host A record and PTR record in the Reverse Lookup Zone in Microsoft DNS, you can follow these steps: To create a Host A record: These steps should allow you to create DNS Host A and PTR records in the Reverse Lookup Zone using Microsoft DNS. Remember to refresh the DNS cache on the client machines for the changes to take effect.
Read MoreCreating a static ARP Entry in Cisco Devices
To create a static ARP entry in a CISCO device, you can use the following command: In the command above, replace <ip-address> with the IP address for which you want to create the ARP entry, and <mac-address> with the corresponding MAC address. Note that the arpa keyword specifies the address resolution protocol type. For example, if you want to create a static ARP entry for IP address 192.168.1.10 with the MAC address 00:11:22:33:44:55, you can use the command: Remember to save the configuration to make it persistent across device reboots:…
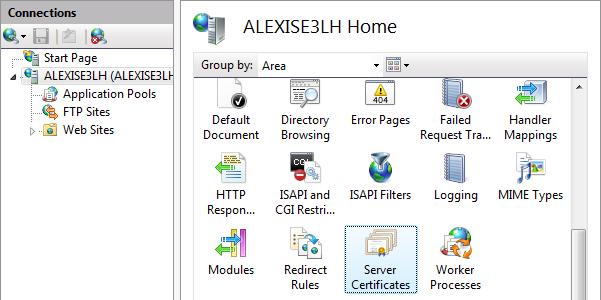
Read MoreCreating and binding self-signed SSL Certificates in IIS
To create and bind a self-signed SSL certificate with PowerShell and IIS, you can follow these steps: Make sure to replace “yourdomain.com” with your actual domain name. The certificate will be stored in the “My” certificate store. Replace “password” with your desired password, and “C:\path\to\certificate.pfx” with the desired path and filename for the exported certificate. Your self-signed SSL certificate is now created and bound to the specified website in IIS. Please note that self-signed certificates are not trusted by default in web browsers and may trigger security warnings when accessed…
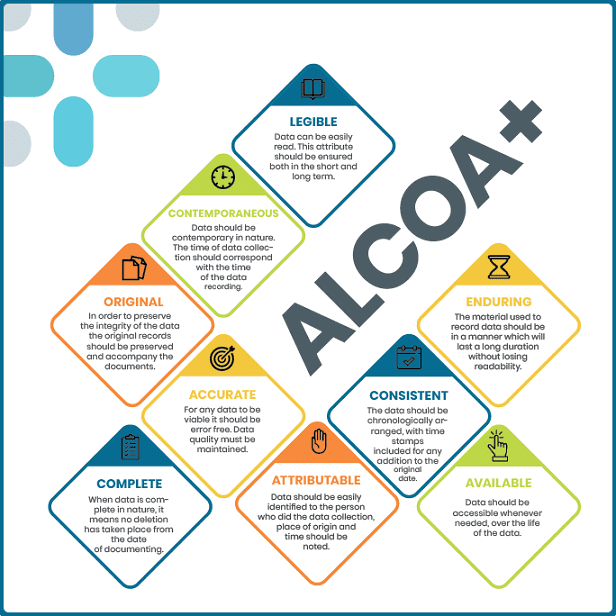
Read MoreALCOA+
ALCOA+ is a quality management framework used in various industries, particularly in healthcare and clinical research. It is an extension of the original ALCOA principles, which are a set of guidelines to ensure data integrity in regulated environments. ALCOA stands for: The “+” in ALCOA+ represents additional principles that enhance data integrity. These principles include: Adhering to the ALCOA+ framework helps organizations ensure the reliability and trustworthiness of their data by maintaining accurate, complete, and unalterable records. By following these principles, organizations can improve data quality, transparency, and compliance with…
Read MoreBasic Cyber Security Principles to Protect MES Systems
Cybersecurity is crucial for protecting Manufacturing Execution Systems (MES) and ensuring the integrity, availability, and confidentiality of data. Here are some basic fundamentals to consider for enhancing cybersecurity in MES systems: Remember, cybersecurity is an ongoing process. Regularly reassess and update your security measures to adapt to the evolving threat landscape.
Read MoreBeyond Compare
I have been using Beyond Compare for over a decade now, and I can confidently say that it has been an indispensable tool in my daily workflow. This exceptional file and folder comparison software has consistently provided me with accurate and reliable results, making it an essential part of my professional toolkit. One of the standout qualities of Beyond Compare is its consistency. Over the years, this tool has continuously delivered outstanding performance, ensuring that I can rely on it for all my comparison and synchronization needs. Its stability and…
Read MoreFiddler Web Debugger
I have been using Fiddler Web Debugger for over a decade, and I must say, it has been an essential tool in my web development arsenal. With its extensive range of features and user-friendly interface, Fiddler has consistently proven its worth, allowing me to debug and analyze web traffic effortlessly. One of the standout features of Fiddler is its robust interception capabilities. Being able to intercept and inspect HTTP and HTTPs traffic has been invaluable in identifying and troubleshooting issues in real-time. Whether it’s analyzing API requests, monitoring network activity,…
Read More